A Little Background
Conflict is inevitable, and as a result, military force is required if a peaceful solution is unattainable. One of the numerous outcomes of this course of action has been the evolution of battle strategy and weaponry. This having the sole purpose of either efficiently defeating the enemy or defending against their attack (countermeasures). The key elements to this evolution are observation, data collection and analysis. Furthermore, this ideally results in the optimization of the assets available. There are numerous analogous examples in the sporting (Figure 1) world of countermeasures—football, boxing, fencing, even chess, etc. But some of the most exciting examples are found in history.

Alexander the Great in 331 B.C. (Figure 2) during his campaign against Persia and emperor Darius at Gaugamela near modern day northern Iraq, was met with overwhelming odds. It is said that the Persians had a million soldiers with 200 scythed chariots. Meanwhile Alexander had half the number of soldiers and no chariots. The scythed chariot was fitted with large rotating blades attached to its wheels and was greatly feared and effective at decimating foot soldiers with ease.

Alexander had two fundamental obstacles, he was outnumbered and out gunned—what to do? Alexander, knowing the typical battle strategies implemented at that time (intelligence) along with observing the battle line formations (situational awareness), developed a strategy that confused the Persians and divided their forces, thus reducing the effectiveness of this advantage. How to deal with the chariots? Alexander, observing the horse’s behavior, realized that when the animal charged towards the battle line it veered towards the path of least resistance. Instead of arranging his soldiers in straight lines he formed them into three-sided box shape configuration and fitted them with long spears. As the chariots approached, the horses would avoid the spears on either side towards the center entering the box or “mouse trap” allowing the soldiers to eliminate the threat (countermeasure). This technique rendered chariots useless and, once word travelled, they were never used again in battle.
Archimedes a brilliant mathematician and inventor who helped in the defense of Syracuse against Rome 214-212 B.C. (Figure 3), developed a counter measure that would capsize Roman ships in the harbor. It was essentially a large crane with a hook, this defended the outer walls from sea-based siege works. This was so effective that Roman crews refused to approach the walls.
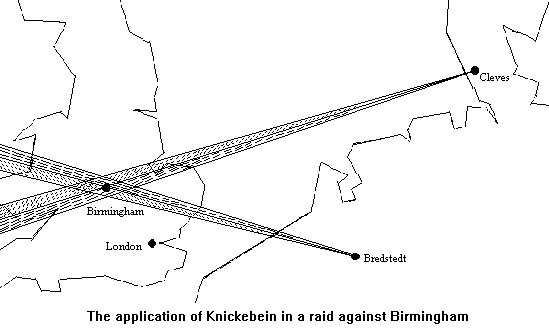
Fast forwarding, during the early stages WWII, Germany launched a very successful bombing campaign against Great Britain, decimating cities. The British were astonished by the accuracy of these bombing runs especial at night. A brilliant scientist, Professor R.V. Jones hypothesized the Germans could be guiding the aircraft by radio beams. He was initially dismissed by the military establishment. However, William Churchill thought it plausible and commissioned the professor to investigate. His suspicions were found correct, the Germans were transmitting beams from two locations inside occupied Europe that converged over England (Figure 4). This was known as the “Battle of the Beams” and was essentially the start of the electronic warfare (EW) battle front. British military developed methods to jam and alter these beams thus rendering them less effective, sending bombs into farmland or into the sea. This, along with implementing radar, changed the course of the war and arguably the fate of Britain.
Electromagnetic Landscape
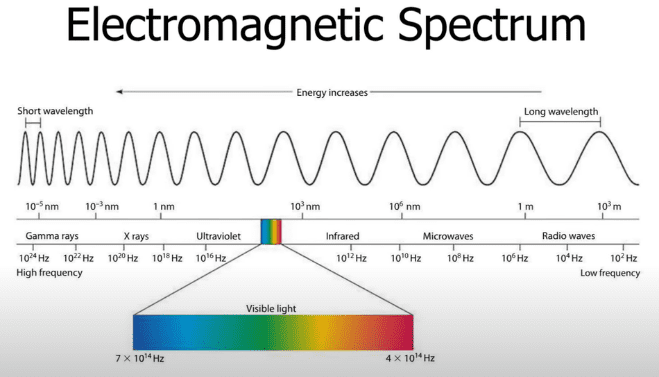
We’ve come a long way from the “Battle of the Beams” with technology that is mind blowing, however, fundamentally, nothing has changed–we are still manipulating electromagnetic (EM) waves. The EM spectrum covers frequency 102Hz to 1014Hz, including visible light (Figure 5). EM waves are produced by applying an electromotive force to a conductor at specific frequency or wavelength causing free electrons to move (current). This movement induces a magnetic field around the conductor and based on the structure and position of the ground plane will radiate this energy into free space (Figure 6). Ideally the radiating structure (antenna) should be a minimum of a quarter wavelength. The shape of this radiating pattern can be designed to focus energy in specific directions or beams (Figure 7).

Some of the tradeoffs between frequency selection are physical size of the antenna and electronic components, resolution as it relates to radar return signature, data rate requirement, and atmospheric attenuation. Atmospheric attenuation increases with frequency as does resolution and data rate. So, as the operational distance increases you can either lower the frequency or increase transmit power.

EM waves are ideal for encoding information through modulation techniques that alter the phase, frequency, and magnitude of the driving waveform. There are broad applications for this behavior from advanced wireless communications, navigation, and radar to name a few, all play an integral role in our daily life.
The Unseen Battlefield!
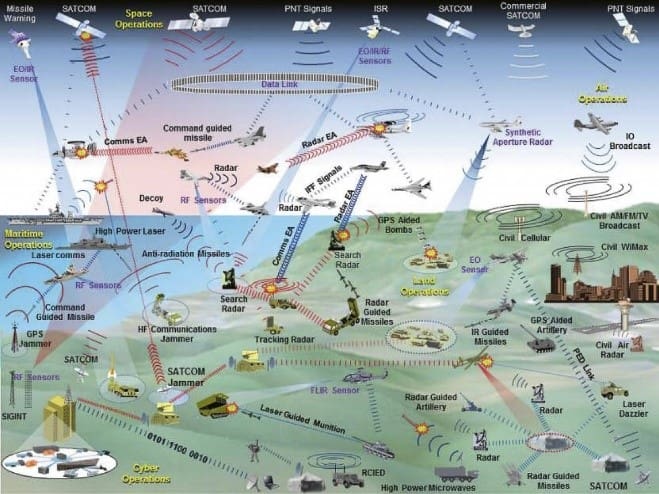
The modern-day battlefield is largely unseen and comprised of a cacophony of EM energy which, if seen, would rival that of Independence Day firework show (Figure 8). You would observe scanning beams, like search lights emanating from land, sea, and air. You would also see waves of light traveling across the surface of the earth and reflecting off the atmosphere, similar to aura borealis. Although unseen, this invisible medium is where battles are won or lost.
It is hard to imagine the complexity of an active battle theater. This comprised of global satellite command and control, real-time synchronized, air, land and sea coordination, radar in all forms with countermeasures throw in the mix. It’s mind boggling!
So, What is EW?

Electronic warfare is the manipulation of the electromagnetic spectrum to provide the reliable operation of friendly command and control while simultaneously disrupting or denying adversarial use of the spectrum. This is accomplished by listening, learning, adapting and attacking, essentially the same timeless principles that have been effective for millennia. The primary areas of EW focus are communications, radar, and navigation. All three incorporate the same basic electronic countermeasure (ECM) elements, jamming, and spoofing.
Jamming is overwhelming a system with directed energy or information to either render it useless or unreliable. Directed energy jamming overdrives the receiver circuitry into compression, making it difficult to recover the desired waveform. With modern day communication systems that utilize spread spectrum and data encoding, jamming is becoming the primary method of disruption.

Other techniques such as chaff (Figure 9), overwhelm the receiver with information by ejecting canisters of metal strips cut to the wavelength of the radar frequency when the aircraft is being actively targeted. This has the effect of scattering the return signal of the reflected wave from the radar pulse confusing the system. One issue with jamming is it can disrupt friendly operations and become an easy target for radar seeking missiles or tracking equipment. An additional method of jamming, as it relates to radar tracking and target acquisition, is to detect radar signatures, sync with the transmit pulse, then broadcast return pulses at varying intervals which are then received by the enemy radar, thus confusing their detection system (Figure 10).
ECM is just the first level of EW. Electronic counter-countermeasure (ECCM) is the development of solutions to the countermeasures and so on and so forth. Electronic support measures (ESM) is a system that listens and records all adversarial EM sources. It then parses it into meta data elements which can be analyzed and referenced for later use.
Drone Wars!

We are all familiar with the use of drones for military operations; most notably, the Predator, which performed its first kill operation by the CIA in February 2002 in Afghanistan. Since then, the Predator has played an integral role in the execution of numerous successful operations. The most recent publicized strike was the targeting of Soleimani by the MQ-9 Reaper, AKA Predator B developed by General Atomics (Figure 11).
Beyond the use of Military grade drones that are highly managed, secured, and traceable, the up and coming threat are commercial and consumer grade drones. These drones are powerful (legal max takeoff weight 55lbs), use secure communications (spread spectrum) and can be untraceable (Figure 12). Drones can be fitted with explosives, deployed in swarms, target hard and soft targets. Clearly an ideal technology for bad actors. On August 4th, 2018, in an assassination attempt, two drones detonated near President Nicolás Maduro in Caracas. One could only speculate that this trend will continue.
Mitigating the Threat?

Current off the shelf (COTS) technology centers on varying levels of directed jamming. Most COTS drones are designed to either return to home or land if the communication link is severed. The issue with either of these situations is the drone behavior can be unpredictable. If the drone is fitted with explosives, losing altitude and detonating in a random location is undesirable to say the least; and if the GPS signals used for navigation are disrupted the drone again could be unpredictable.
The ideal solution is to gain control of the drone; this addresses all potential risks including swarms. In order to implement this strategy, you need critical intel about the communication link, specifically frequency bands, modulation, and data encoding. Fortunately, this information is not classified unlike the Predator and readily available to the public. However, this is no easy task, you still need to implement an ESM system to form a database, actively study COTS drone products, monitor and track EM activity, identify threat, and attack. The system needs to be frequency agile and capable of covering all current bands, such as 900 MHz, 2.4 GHz and 5.8 GHz.
There are several companies implementing this type of solution and have had varying degrees of success. However, the threat is real, and diligence is required to meet the challenge. NuWaves is playing a critical role in this industry by providing cutting edge broadband, bidirectional power amplifiers and filtering systems and is well positioned to address this market.
References
-Figure 1 – National Football League (NFL)
– Figure 3 – https://en.wikipedia.org/wiki/Claw_of_Archimedes
– Figure 8 – https://www.japcc.org/electronic-warfare-the-forgotten-discipline/
– Figure 9/10 – Covert Cabal – Electronic Warfare – The Unseen Battlefield
– Figure 11 – https://www.youtube.com/watch?v=drUcrbcrJSw
– Figure 12 – https://www.unmannedsystemstechnology.com/company/ggs-gmbh/
– https://en.wikipedia.org/wiki/2018_Caracas_drone_attack https://en.wikipedia.org/wiki/General_Atomics_MQ-9_Reaper https://www.digitaltrends.com/cool-tech/history-of-drones/
– Prof. Shlomo Maital – how to innovate, how to track global markets
– Rupert Matthews – Siege of Syracuse Punic Wars [214–212 BCE]
– Reginald Victor Jones – The Wizard War



Comments are closed