Our Digital World

Information comes in many forms, from ancient hieroglyphs to seemingly endless streams of 1 and 0’s that form the foundation of our digital world. Prior to the digital age, information or data was stored in vast arrays of voluminous filing cabinets, binders, and folders that required human interaction to manage or access. Since the advent of the computer, data storage has evolved from punch cards, to magnetic floppy disks, local hard drives and servers to massive cloud-based data farms. As the world has migrated for the obvious reasons to digital media, our data is ever more vulnerable to nefarious activity from bad actors.
Cybersecurity

It seems like a daily occurrence when we hear “whoops a data breach exposed millions of people’s personal information” and or “another computer virus has struck again!” As a result of these attacks, an industry has developed which has grown in proportion to this ever-increasing threat, cybersecurity. Cybersecurity found its beginnings from a research project in the 1970’s. A researcher Bob Thomas realized a computer program could propagate across a network and leave behind a small trail wherever it when.

He named the program Creeper and was designed to travel between Tenex terminals. The program was generally harmless and would simply print the message “I’m the creeper: Catch me if you can”. It was later modified by Ray Tomlinson, the inventor of email, to replicate itself, rather than simply move, and is generally accepted as the first computer virus. Later he wrote a program named the Reaper, that would find and delete the Creeper; thus, the start of the first antivirus software.

Cyber threats continued to grow from their early beginnings and steadily expanded into the Cold War, an example being a hack perpetrated by a German computer hacker, Marcus Hess. Hess hacked an internet gateway at Berkeley where he gained access to hundreds of military computers including the Pentagon. He was caught by Clifford Stoll in 1986 who was a systems manager at Berkeley National Labs. Stoll was trying to correct an $.75 accounting error and discovered the hacking activity.
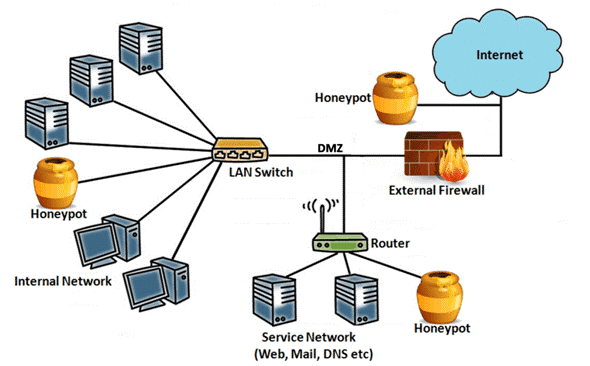
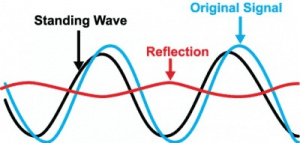
Hess was later caught and prosecuted by the German authority for selling secrets to the KGB. Stoll caught Hess by implementing a hacking countermeasure known as a “honeypot”. A honeypot is an intentionally exploitable computer or network segment that is monitored for hacking activity for intel purposes. The adversary’s techniques and possible origin can be determined, additionally counterattacks can also be implemented. Today’s cybersecurity threat is broad and deep and can affect anything from banking to power grids, communication systems and networks, internet stability, military and avionics systems, etc. Our entire world is vulnerable to this threat—scary stuff.
What is Hacking?
Hacking is typically a nefarious activity intended to unlawfully gain access to electronic systems by exploiting hardware and or software vulnerabilities. Hacking comes in many forms and can be as simple as someone figuring out your password, to exploiting a hardware bug in a processor used in the system. A great example of a recent hardware vulnerability was discovered in 2018 known as Spectre, which affected a broad range of modern CPU’s from Intel, AMD, IBM, and even some ARM processors.
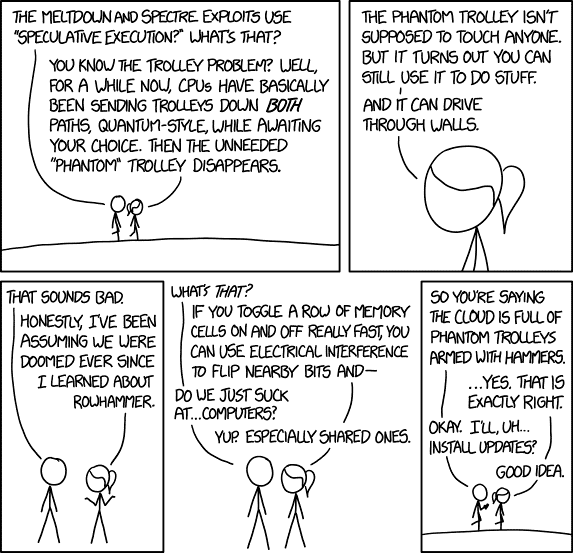
This vulnerability allowed access to vital data at the system cache level through scripts that could be exploited by hackers, Microsoft had to develop a patch to resolve this issue.
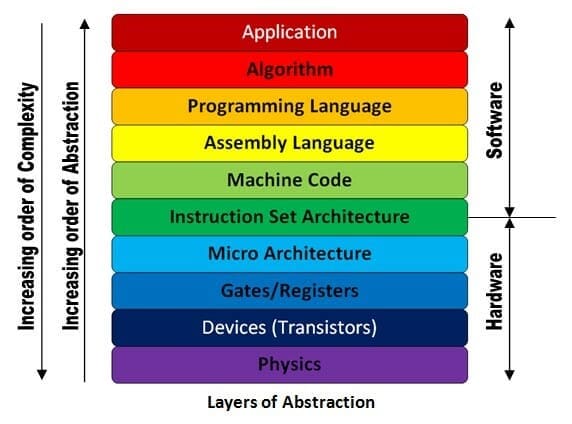
Electronic systems are comprised of a myriad of devices with varying degrees of complexity that require firmware to function and interact with the main CPU. As the example with Spectre suggests, hackers are extremely sophisticated and study systems to the device level, even exploiting the operational code (Opcode) of the chipset and firmware drivers. Typically, exploitation of computer systems occurs from the micro architecture to the application layer (figure 8). Additional points of weakness are system data buses and I/O connections.
Minding Your Own Data Bus
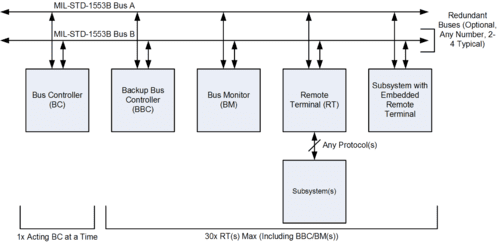
A data bus system that could be vulnerable to exploitation if not properly protected are test ports in avionics, specifically MIL-STD-1553. This is a master / slave bus system used within the aircraft that connects all internal systems and sub-systems critical for proper operation. Test ports are available at various access points throughout the aircraft for system checks and diagnostics. It is possible to disrupt data signals by monitoring and corrupting bit patterns and spoofing critical subsystems within the aircraft. Proper protection to restrict the direction of data on the bus while extracting valuable data necessary for inflight diagnostics.
Partnering with the Air Force Research Laboratory, NuWaves has developed two product variants that address MIL-STD-1553 test port cyber threat, Vegas-S and Vampire.
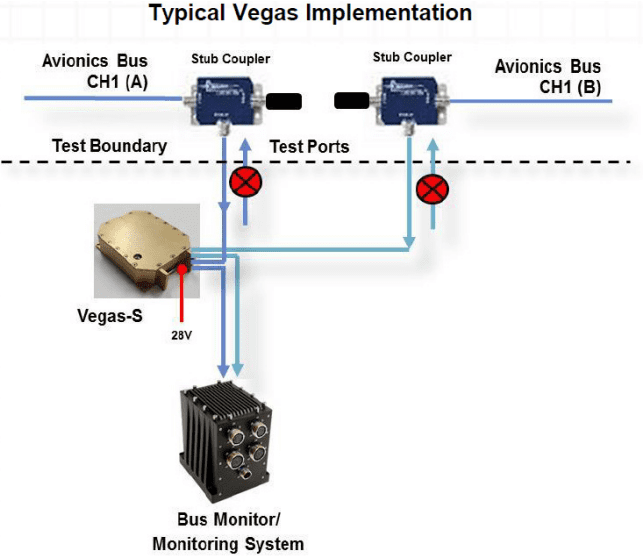
Vegas-S is essentially a data diode restricting serial bus traffic to propagate in one direction, receive mode. Thus, providing hardened security, functioning as hardware firewall that cannot be exploited by cyber-attacks.
Key Features and Benefits:
• Simple single chip solution
• No microcontrollers or processors that could be maliciously altered
• Very low input to output latency
• Protect against an LRU failure or voltage transient
• Reconditions the MILSTD-1553 signal for driving at least 200 feet of MILSTD-1553 cable
• Subjected to MIL-STD-810G, MIL-STD-704F, and MIL STD 461 tests
Vampire provides the same functionality as Vegas with the added feature of being a data recorder. Vampire provides up to 10 hours of data recording and could be utilized for an array of bus monitoring activities including: predictive maintenance, reverse engineering, anomaly detection, and as a real-time secondary display.
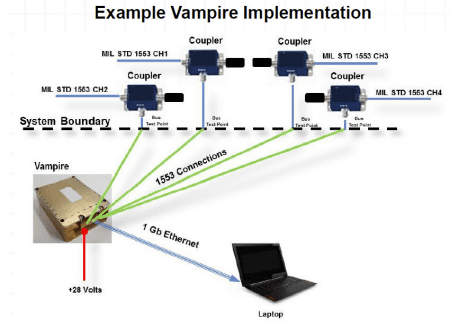
Key Features and Benefits:
• Decodes incoming 1553 traffic
• Creates timestamp for bus controller (BC) command message at 5 ns
• Measures remote terminal (RT) response time to 5 ns
• Packetizes 8 BC and RT responses into a UDP packet for transfer efficiency
• Sends all decode data in UDP format out of Ethernet port
• Can be used with commercial off-the-shelf (COTS) Ethernet tools
It is clear that cybersecurity threats are pervasive, and safeguards are necessary to combat this form of attack. The cyber landscape is the battlefield of the 21st century and NuWaves is dedicated to providing innovative solutions to address this treat.
References
– Figure 1 – https://www.timesofisrael.com/israel-pushes-ahead-with-tender-for-massive-cloud-based-data-center/
– Figure 2 – https://www.kaspersky.com/resource-center/threats/virus-delivery-methods
– Figure 3 – https://history-computer.com/Internet/Maturing/Thomas.html
– Figure 4 – https://www.newsweek.com/history-computer-hacking-69449
– Figure 5 – https://cyberhoot.com/cybrary/honeypot/
– Figure 7 – https://www.explainxkcd.com/wiki/index.php/1938:_Meltdown_and_Spectre
– Figure 8 – https://www.secplicity.org/2018/09/19/understanding-the-layers-of-a-computer-system/
– Figure 9 – https://en.wikipedia.org/wiki/MIL-STD-1553